With many cyberattacks and fraud campaigns today, the threats detected by risk and fraud teams are often only the tip of the iceberg. Most risk and fraud teams have yet to see the range of attack vectors that are available to attackers, who are harder than ever to spot due to the widespread use of device emulators, proxies, and other cloaking tools. With this in mind, we built an attack simulator capable of mimicking known attack MOs. The simulator is now available and can be previewed on demand by anyone who wants to experiment with and explore the impact of different attack scenarios.
Within the Transmit Security Admin Portal, users can access the attack simulator to understand how emerging threats might affect them and the best approach for investigating those attacks.
Using the “Simulate” tab of the new UI tool, users can select from a range of attack types to create custom simulations by selecting and inputting different values, including:
- Attacks from bots, emulators, spoofed devices and virtual machines
- Requests from different moments in the user journey, including login, registration and transactions
- Number of requests and other parameters, such as the number of unique devices, IP addresses or user agents.
Users can experiment with these settings to create a wide variety of simulated attacks, as shown in the screen below.
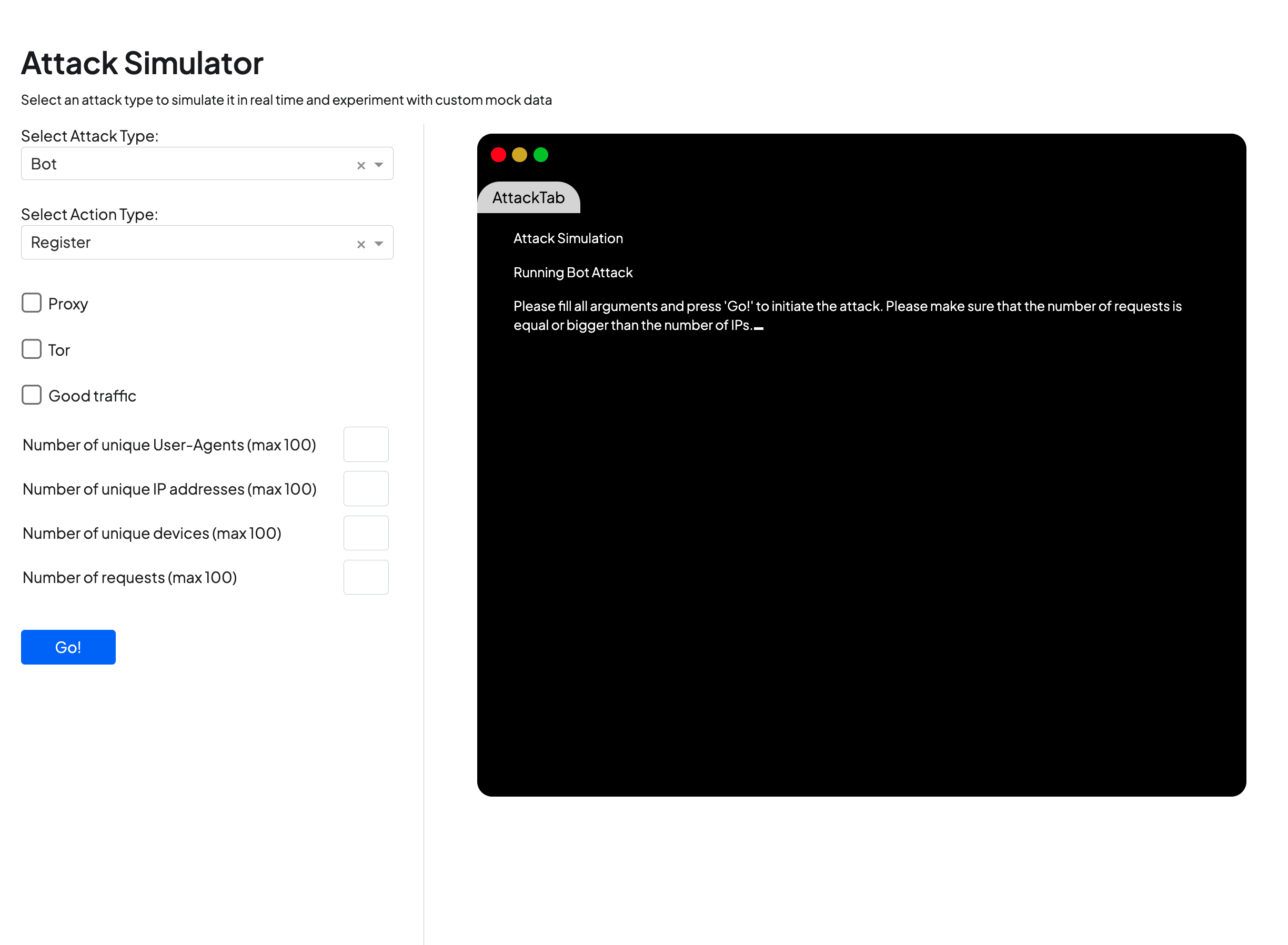
With the ability to check for traffic coming from proxies, tor networks and legitimate traffic, users can not only view the characteristics of a specific attack, but how those characteristics differ from known good traffic.
Once the parameters for the simulation have been selected, simulated traffic is fed into the user tenant in the Recommendations view, where users can investigate the attacks and see how they are captured within our Detection and Response service. The service, which analyzes a broad range of telemetry and multiple detection methods, delivers its findings in real time as transparent, contextual recommendations for relevant requests throughout the user journey — showing not only how individual requests should be handled, but specific risk and trust signals that led to that recommendation.
Below, you can see a screenshot of the overview page available from the service. With the ability to visualize highlights, summaries, visualizations and a breakdown of key statistics, analysts can quickly gain an understanding of new trends that may signal suspicious traffic, such as a surge in bots or risky IPs.
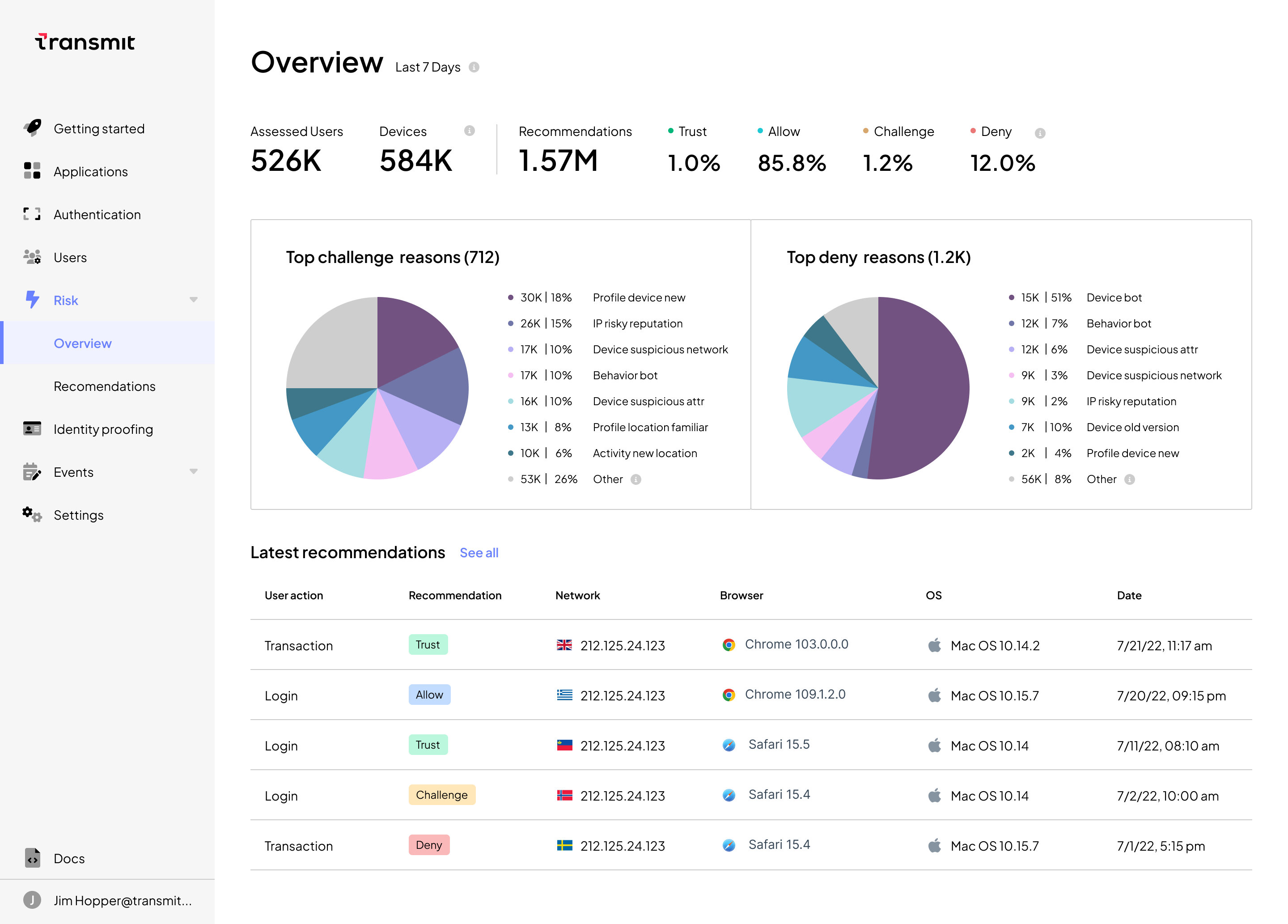
Within the UI, analysts can explore the simulated data by:
- visualizing overall trends, such as common reasons for deny recommendations
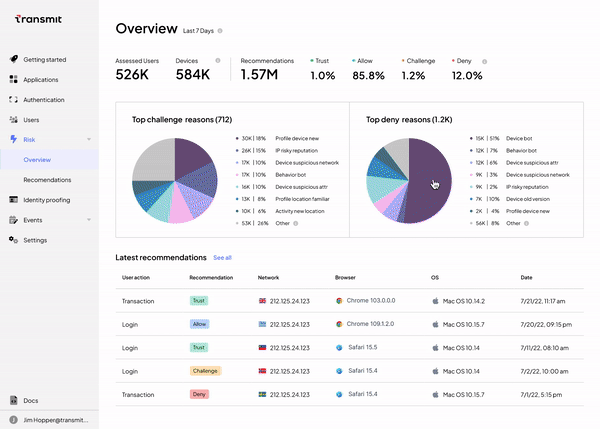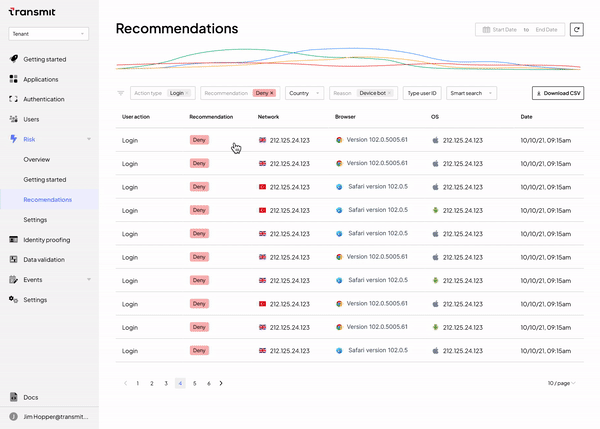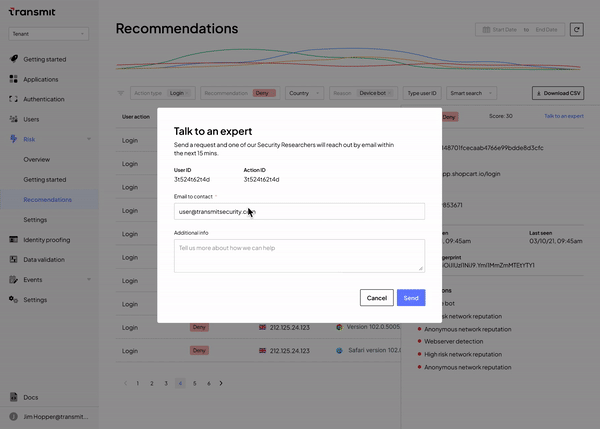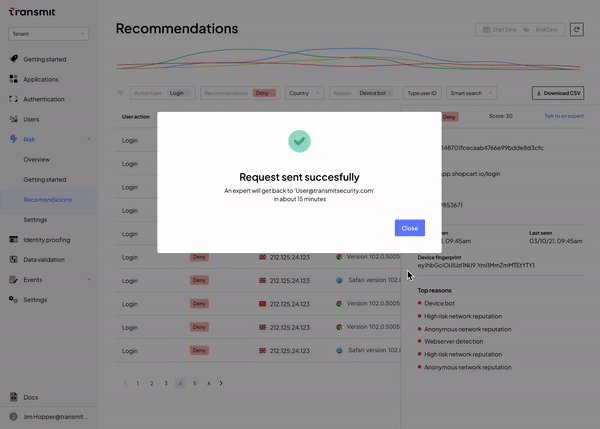
- viewing a list of recent requests and Detection and Response recommendations for handling those requests
- drilling down into specific recommendations to understand the key factors that led to the decision, such as the use of proxies, emulators or known bad IPs
- filtering for specific moments in the user journey, such as registration or login, or for specific recommendation types, in order to better understand attack patterns
- exporting to CSV to explore offline or create reports based on these metrics to share with colleagues
- contacting an expert at Transmit Security for further discussion
This lets users exploring the service via our attack simulator can use the UI to get a concrete understanding of how fraudsters are operating — an increasingly difficult task as attacks become more sophisticated. For example, a recent blog on detecting registration bots details a case study where bot attacks originating from only a handful of devices were able to use device spoofing and hosting IPs in order to create 2000 fraudulent new accounts using only 10 unique devices.
Detecting this kind of attack is a complex task requiring the use of multiple detection methods — a challenge we’ve been working to solve with Detection and Response. And by using the attack simulator tool to visualize how different attack MOs and patterns appear on the Transmit Security Platform, users can gather data to illustrate the specific challenges they’re facing, share that data with stakeholders and gain a direct line to our experts to quickly gain support in managing risk.
So whether you are experimenting with mock data created by the simulator or experiencing a real-life attack, you can use the Transmit Security Admin Portal to gain a self-serve, rich UI experience that can educate, train and enable teams on:
- how emerging threats might affect their applications and services
- the impact of different attack types (bots, spoofed devices, VMs or emulators)
- how to resolve different attacks by developing approaches for investigating them
- the different ways in which different attacks may impact different moments in the user journey (e.g., login, registration and transaction).
The attack simulator will soon be available via public website to all users, but is now available in preview upon request. To request a free preview of the tool and demo of Detection and Response, contact our experts today.



