The rise of registration bots
The past few years have witnessed a massive increase in new account fraud across a wide range of digital platforms. From fake profiles on dating apps that send phishing messages to legitimate users to bogus online gaming accounts designed to accrue in-game assets, to fraudulent financial accounts created to open new lines of credit, these phony accounts are often driven by registration bots — a type of bad bot that uses stolen or synthetic identities to create fraudulent new user accounts for malicious purposes. From 2020 to 2021, new bank account fraud grew 64%, according to the FTC.
The direct and indirect losses that result from new account fraud have a huge impact on the wider digital ecosystem, costing businesses almost $7 billion in 2021, according to Javelin Research. As a result, it’s crucial that businesses stop these accounts at the front door — but doing so is becoming increasingly difficult as bots become better at evading detection. This blog post will explain how Transmit Security used a sophisticated combination of multiple detection methods to uncover thousands of registration bots in an attack on one of our customers, resulting in a 98% reduction in new account fraud and a 500% increase in bad bot detection.
Identifying suspicious activity
The customer in this case study is a large U.S. bank that mainly leverages our services in their login flow. Although our platform was not directly integrated into their registration flow, we offered to help when we heard they were experiencing a large number of account creation attacks.
The bank shared with us 2000 examples of accounts created within a short period of time. These accounts were deemed suspicious as each new account was created using an address located far away from the geolocation of their IP, which typically have a strong correlation. And although the IP addresses used in the attack were not known to be malicious, each registration came with a fresh IP address and a fresh device with no history of cookies — another red flag, considering that most users’ devices contain some history of activity.
Deepening the investigation with multi-method detection
Recognizing registration bots relies on our ability to identify suspicious attributes and behavior during the account creation process. Fortunately, we had collected telemetry as part of the bank’s current integration of their login flow. Using this data, we discovered that these suspicious registrations included other signals that could be used to identify this attack a priori based on the network reputation, device velocity and behavioral biometrics.
Network reputation
Let’s start with the network. A big portion of those account registrations came from hosting IPs, which indicates that the users were masking their original location. In addition, the attackers were able to evade detection by never using the same IP more than once. This allowed them to circumvent IP velocity checks — a type of control designed to prevent bots by blocking repetitive actions, like multiple account creations, from the same IP address.
Device action velocity
Similar to high-velocity IP activity, high-velocity device actions are another strong indicator of bot activity. And while most security controls will block repetitive actions from the same device, bots are increasingly able to cloak — or spoof — their devices to get around these types of controls.
Our team was able to detect the attackers’ spoofed devices based on their device fingerprint: a device identifier calculated based on a proprietary combination of telemetry signals, such as device attributes, device settings and device usage. The information we collected about these devices’ OS, browser version, screen resolution, time zone and IP address were used together to calculate device fingerprints for the suspicious accounts, revealing that thousands of new accounts had been created using less than 10 different devices. Those are some superhuman users or one busy bot!
Behavioral anomaly
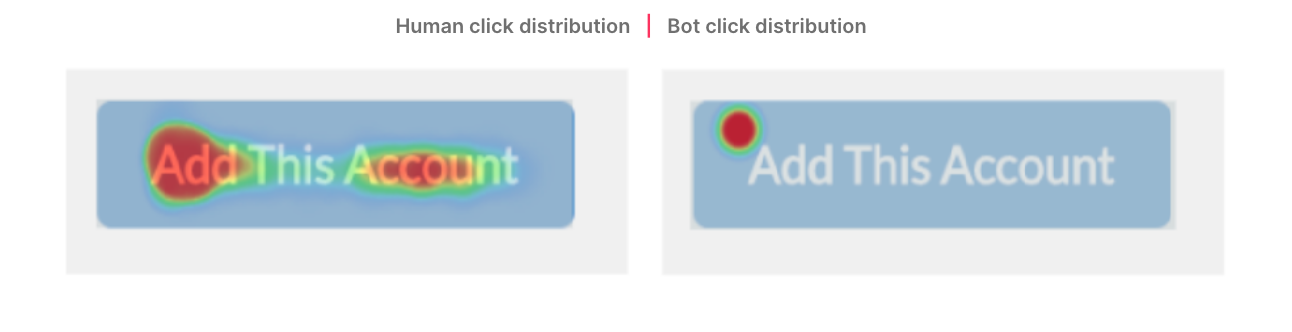
The users’ interactions with their devices during the registration process also provided a strong indicator of bot behavior. For starters, the mouse interactions of bots differ significantly from those of humans. While human users click buttons in different places, bots always click the button in the exact same location, as shown below in a heat map of the registration button.
We detected another suspicious behavior in the registration flow used during this attack. Rather than performing the bank’s full onboarding experience, the accounts were created via an unusual user journey that started in the middle of the onboarding process, but still performed the critical steps required for registration. In the heat map below, you can see that bots are very deliberate in their movements, and do not make any unnecessary clicks or mouse movements during their interactions. In contrast, humans need to read or skim a webpage to understand what’s needed to accomplish a task, resulting in movements that are much less focused and more widely distributed.
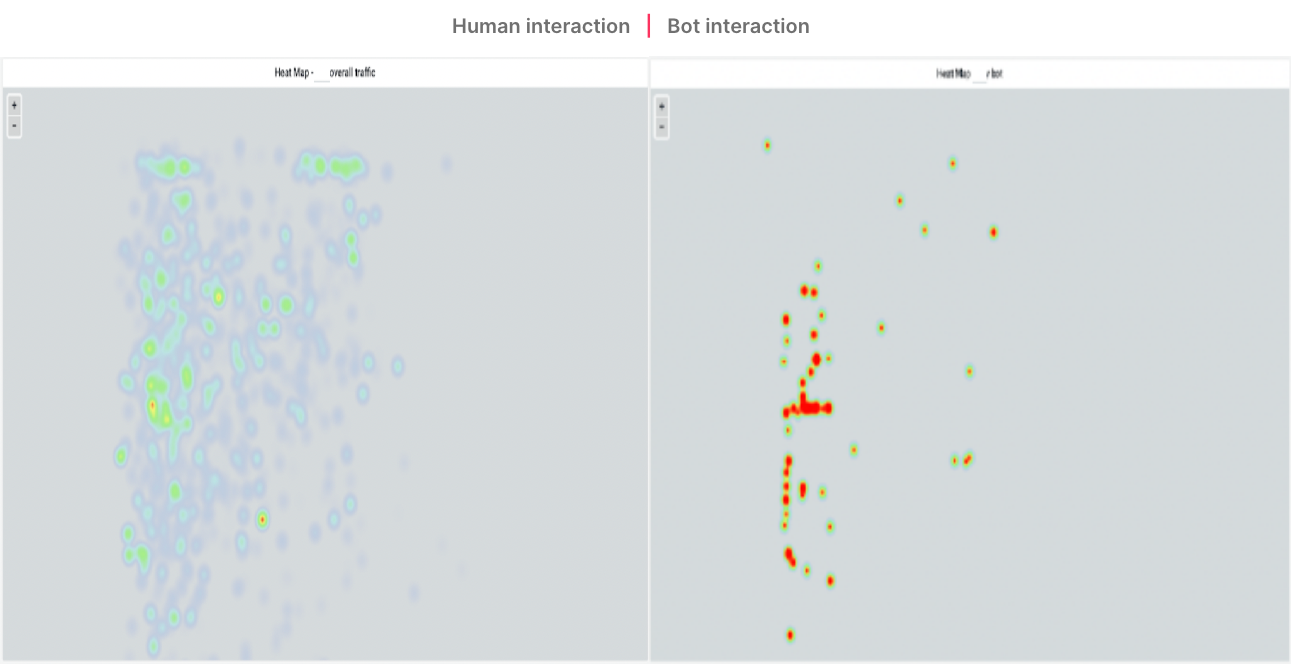
By evaluating all of these indicators together, we were able to uncover thousands of other new account registrations that followed the same pattern. These registrations were later confirmed by the bank’s fraud analysts to be part of the exact same attack!
Advanced detection for evasive bots
In this case study, we were able to significantly expand the detection of registration bots by combining multiple detection methods, including device fingerprinting, network reputation and behavioral biometrics. As bots become increasingly sophisticated, it is increasingly rare that a single risk signal will provide adequate confirmation of a bot attack — and without the ability to confirm bot attacks, businesses risk introducing unnecessary friction for legitimate users and blocking good bots that assist with SEO, social networking and site aggregation. These advanced bot detection capabilities are part of our Detection and Response Service, which uses machine learning to correlate and analyze a broad range of telemetry and multiple detection methods and deliver actionable recommendations on risk and trust at each moment of the user journey. With Detection and Response, businesses can not only protect themselves against registration bots, but ATO, price scraping, inventory hoarding and a range of other fraudulent activities that compromise the security of businesses and their end users.



