Smash Security Threats Like Pro!
Transmit Security is serving up unbeatable protection – and custom pickleball paddles at RSA 2025. Book a meeting to grab yours and take your security game to the next level!
A mobile emulator is software that mimics the hardware and software functionalities of smartphones. Although they have legitimate uses, such as developing and testing mobile applications or replicating the experience of using different gaming consoles, emulators are increasingly used by cybercriminals to bypass security measures by masquerading as legitimate and trusted devices.
This blog will review the fraudulent activities emulators enable and provide three techniques that we’ve developed in the Transmit Security Research Labs to combat this rising threat.
As a fraud tool, emulators can be used by cybercriminals in different ways:
With these threats in mind, we’ve researched the most efficient ways to detect fraud from widely used emulators.
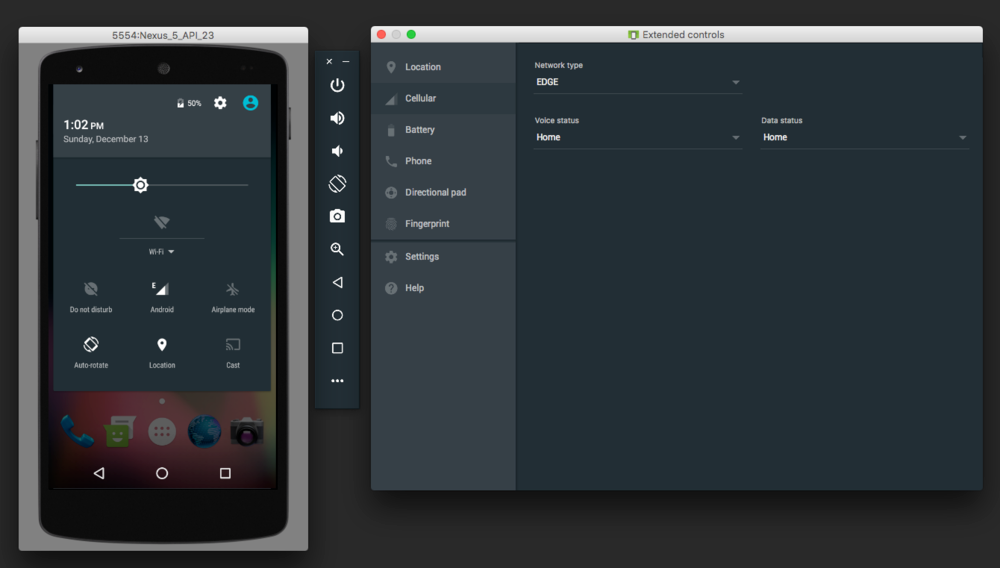
To collect data, we used several emulators that pretended to be different mobile devices and “shopped” them through our demo application. In the example below, you can see how a cybercriminal could emulate a mobile device with just one press of a button.
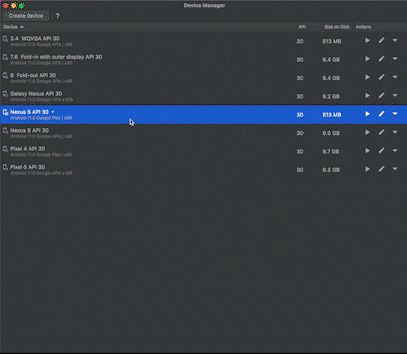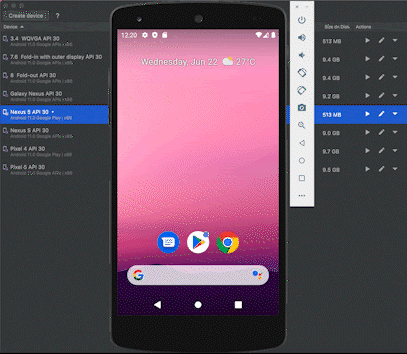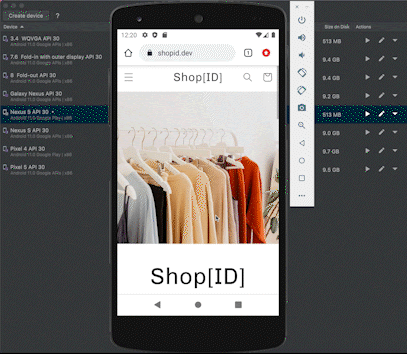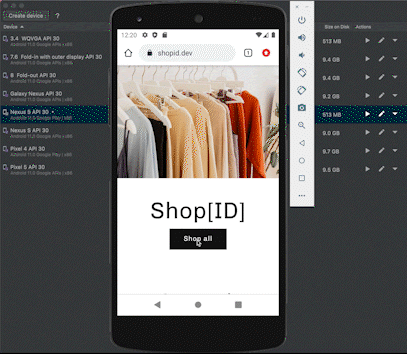
We then analyzed the event data from our experiments to identify anomalies that indicate the manipulation of device attributes. In other words, we tried to differentiate between how a real mobile device behaves compared to a mobile emulator in order to determine the risk signals that might indicate fraudulent usage.
In our research, we found that most of the commonly known emulators have specific “emulator” expressions in their user agent string or Web Graphics Library (WebGL) — a standard API that is used in many popular browsers for rendering 2D and interactive 3D graphics on the web.
When a new device event is created, we search for these expressions using regex, or regular expressions, which are sequences of characters that specify match patterns in text. If there is a match, we can declare the device as an emulator.
In addition, other APIs can be used to detect indicators of emulator usage. Two examples of these are the Battery API and WebUSB API:
In addition, collecting and analyzing information about the device build that is extracted from system properties can provide additional indicators that an emulator is being used. Information that can be collected includes hostname, manufacturer, model name, board type, fingerprint value, hardware, and more.
In the table below you will find emulator common build information values:
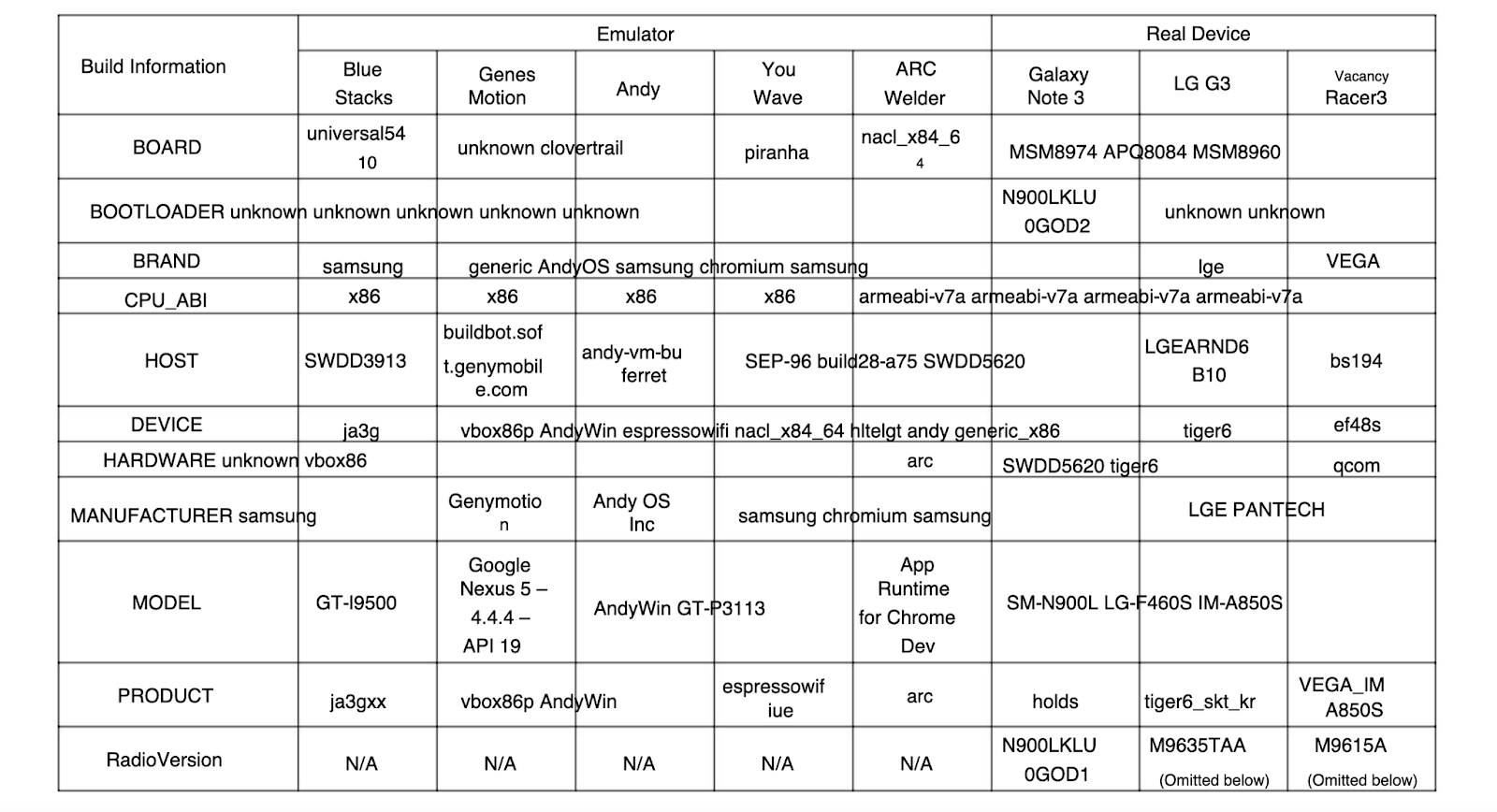
However, it’s important to note that device build information can be easily changed by more advanced cybercriminals and may require additional detection methods to detect evasive tactics used to disguise emulators.
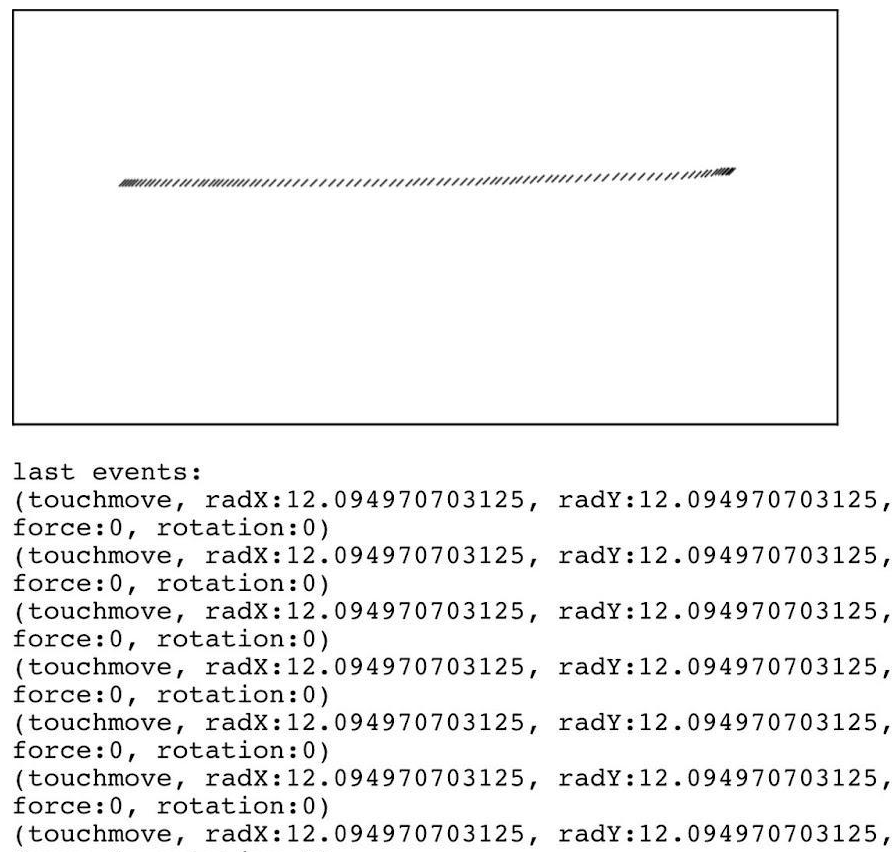
To provide quality support for touch-based user interfaces, touch events offer the ability to interpret finger or stylus activity on touchscreens and trackpads by examining the radius property in touch events.
The radius property is the radius of the ellipse which most closely circumscribes the area touched by a finger or stylus along the axis indicated by its touchpoints. This value, in combination with the radius and rotation angle, constructs an ellipse that approximates the size and shape of the area of contact between the user and the screen.
As you can see below, mobile devices generate the radius when an end user draws a line.
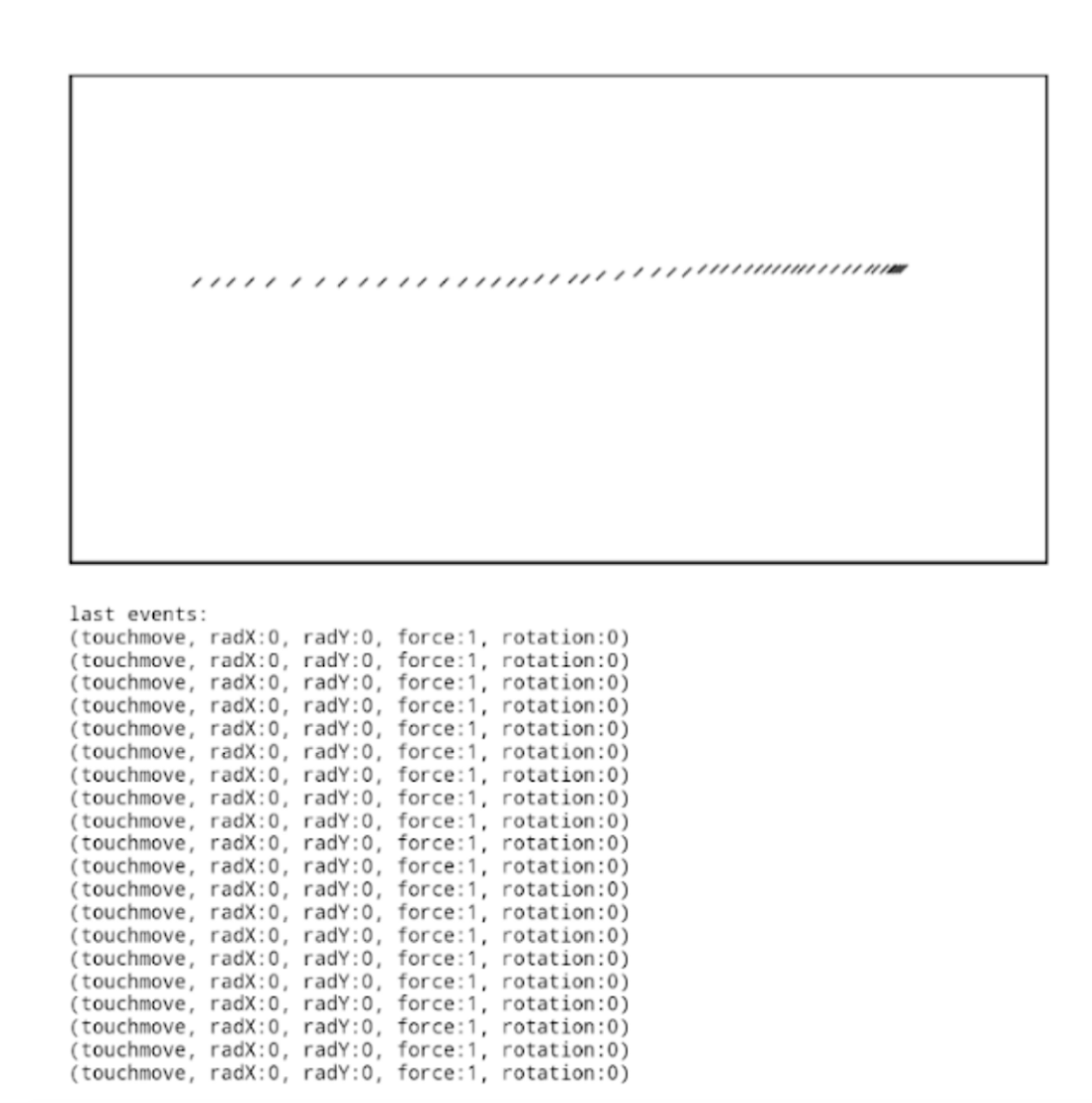
This is not the case with mobile emulators, where there is no contact between the user and the screen, as shown below.
The information connected to a call and SIM can be collected in a mobile operating system. With mobile devices, we expect to receive data on the SIM operator, SIM state and more. Emulators, however, provide different results that may be missing this data, as you can see in the chart below.
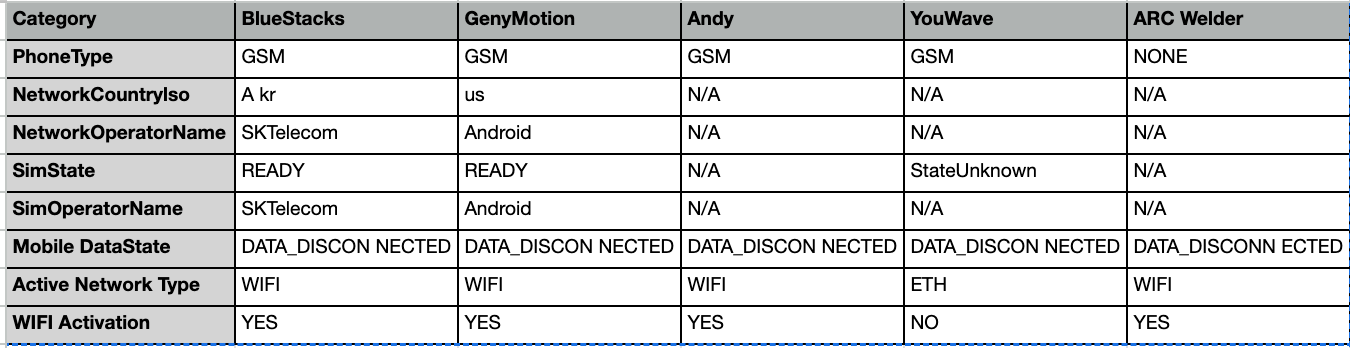
In our research, we devised several detection methods to identify when an emulator is used. The detection methods cover multiple angles, including device reputation, behavioral analysis and SIM/carrier reputation.
However, security leaders and fraud analysts should keep in mind there is no “best” detection method that can be used on its own to indicate the use of emulators. As emulator settings become increasingly configurable, you can expect to see an increase in evasive tactics that will require a combination of methods to optimize detection rates.
Transmit Security’s Detection and Response Services guards against this possibility by combining all of the above-mentioned detection methods to provide a protective canopy and prevent emulator fraud. With this service, security leaders can confidently detect the most advanced tactics used to disguise emulator use, drill down into specific cases where emulators are detected and view trends that can indicate a change in emulator usage over time.
To see it in action, security leaders and fraud analysts can use our attack simulator to explore how emulated and spoofed devices might appear in a wide variety of simulated attacks. To request a free preview of the tool and demo of Detection and Response, contact our experts today.