
It’s Time for IAM to Lead the Cyber-Resiliency Charge
I’m sick of headlines about leaked data, leaving me to wonder if my username, password or private information is listed for sale on the dark web (of course it...
Our modern identity services are exposed through developer-friendly APIs, SDKs and Low-Code services to deliver the scale and performance required for any and all customer use cases.
Featured Blog Post:
I’m sick of headlines about leaked data, leaving me to wonder if my username, password or private information is listed for sale on the dark web (of course it...
Typical identity-related steps implemented by applications
Integration: Low code tools and developer-friendly APIs & SDKs
APIs, SDKs & Low Code
Detection & Response: Real-time risk and fraud prevention
Orchestration: Out-of-the-box decisioning rules & drag-and-drop journeys
Onboarding
Login
Access
Identity Verification:
ID and selfie analysis
Authentication:
Passkeys, Passwordless & MFA
Identity Management:
User Profiles, Authorization, SSO
Cloud-Native Architecture
Our modular identity services are exposed through developer-friendly APIs using cloud-native architecture to deliver the scale and performance required for any and all customer use cases. Quickly build digital identity journeys with security that enhances user experience and bolsters customer loyalty. Protect your customers. Earn their trust. Grow your business.
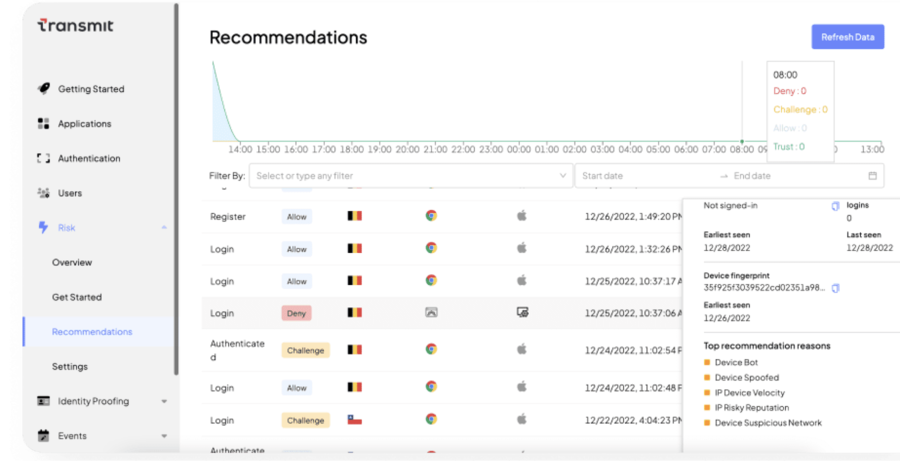
Automatically collect signals about potentially compromised accounts or sessions and only ask users to re-authenticate or add authentication steps when a real risk is detected. Transmit Security offers the most advanced Risk, Trust, Fraud, Bot, and Behavior (RTFBB) engine.
Using our engine, you can protect your customers and minimize friction. Depending on your risk profile and regulatory environment, you can easily choose the type of authentication your customers would need to go through when different risks are detected. We’re cyber security and fraud experts and can provide your customers with the ultimate frictionless yet secure experience.
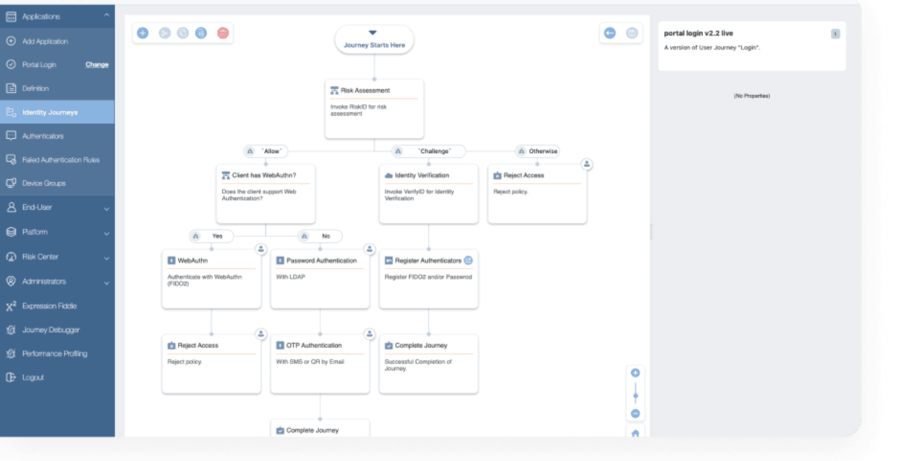
Identity Orchestration is an essential service for managing and securing digital identities in complex and dynamic environments. With Identity Orchestration you could build workflows for customer onboarding, customer login, risk-based authentication and more. You can set policies, tweak the customer experience, choose authentication methods that work for your customers, and do all of that in configuration instead of code.
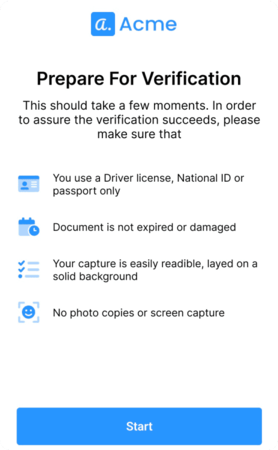
Verify legitimate customers quickly. A deep yet fast document inspection examines every detail to discern if the ID is authentic and unaltered. Biometric matching compares the selfie and ID photo to determine if they match. Automated background checks rapidly screen AML & PEP watch lists, so you don’t have to.
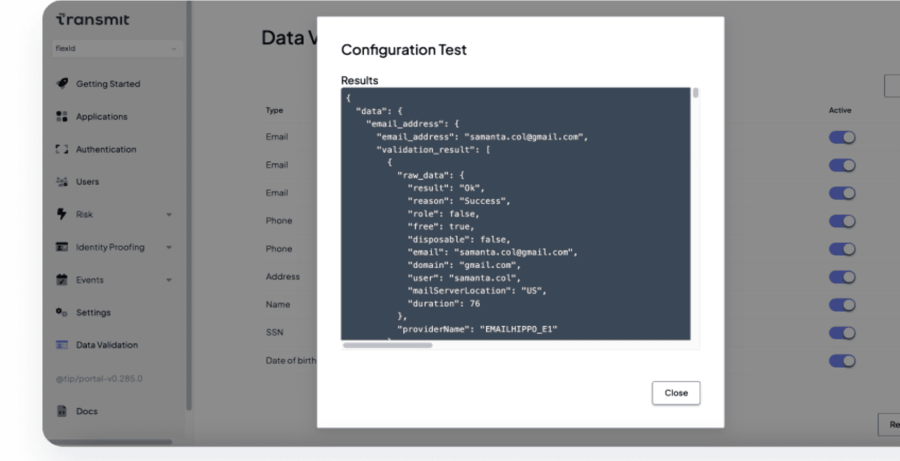
Instantly validate customer identity details. Automate background checks for accurate results in a split second. Transmit Security’s Identity Validation API easily connects to external data sources as well as your own internal data to validate identities and build a comprehensive customer profile. The service simplifies and expedites account registration to comply with global regulations, stop fraud and protect your business.
Choose between passwordless and passkeys, social login, magic links, or passwords. Decide which login options are available to your customers and easily add more options. You can go completely passwordless or try a hybrid of password and passwordless options. Transmit Security supports a variety of Multifactor Authentication (MFA) options, such as OTP and passkeys. Design the perfect MFA experience for your applications and customers based on your UX, security, and regulatory requirements.
In order to support a continuously growing user-base and seasonal or occasional surges in usage, Transmit Security has built a modern microservices-based Customer Identity and Access Management solution, which is able to auto-scale any of the core authentication, user management and authorization services and enable smooth business continuity.
Provide uncompromising security, fraud prevention and customer experience with modular, orchestrated identity services.