Smash Security Threats Like Pro!
Transmit Security is serving up unbeatable protection – and custom pickleball paddles at RSA 2025. Book a meeting to grab yours and take your security game to the next level!
Transmit Security is serving up unbeatable protection – and custom pickleball paddles at RSA 2025. Book a meeting to grab yours and take your security game to the next level!

Uncover the hidden vulnerabilities AI agents introduce, and what fraud teams must do to survive the shift.
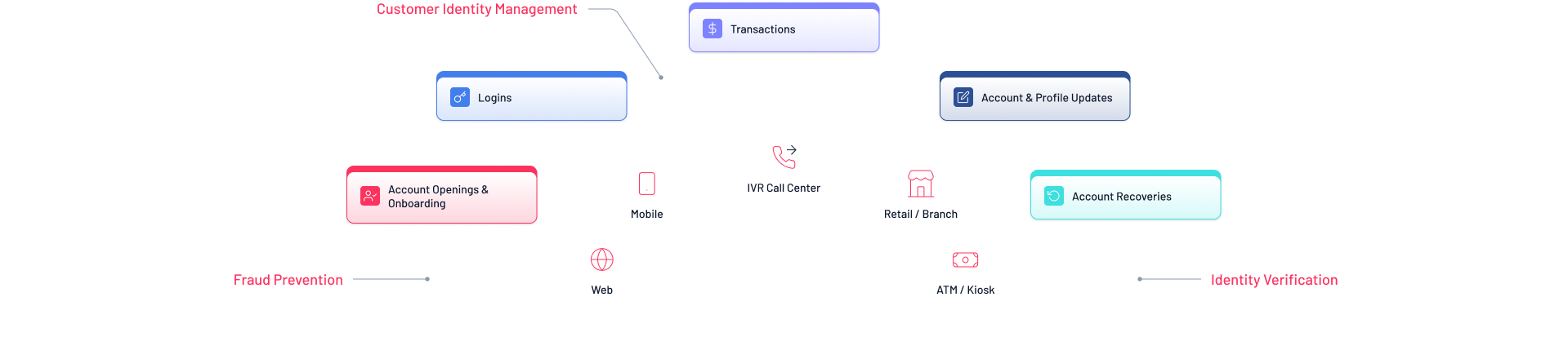
Mosaic by Transmit Security unifies identity management, fraud prevention, and identity verification to stop fraud, enhance user experience, and reduce complexity and costs—delivering the industry’s most resilient CIAM.

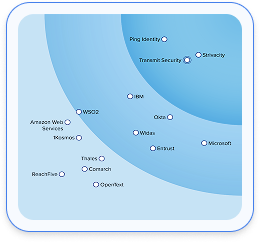
The only vendor recognized by leading analyst firms across CIAM, fraud prevention, and identity verification for its proprietary solutions.

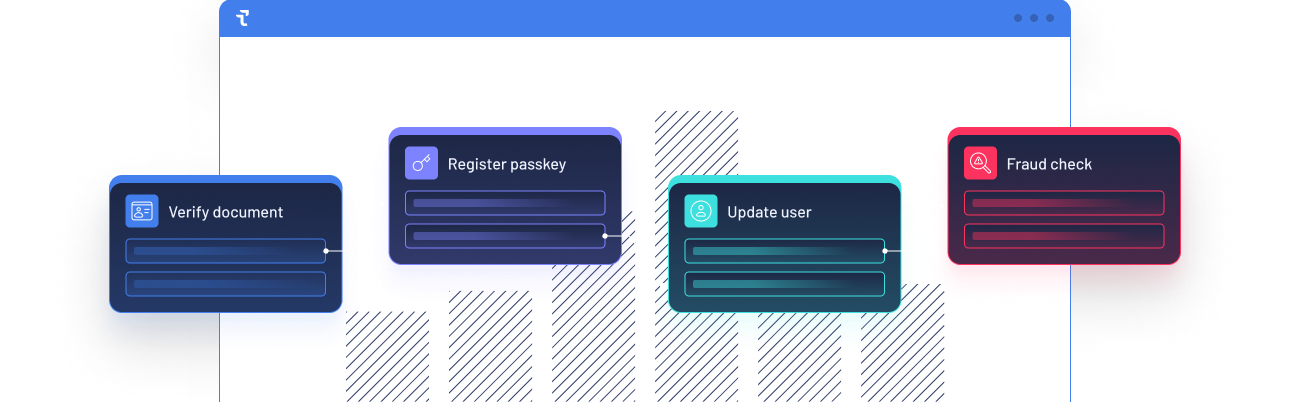
For the first time, a unified enterprise-grade platform that includes best-of-breed fraud prevention, identity verification and identity management. Stop toggling between and normalize events from various sources. Focus on visible, tangible value for your organization.
Mosaic for B2C Identity is designed to deliver frictionless and secure access for consumers at scale. By combining passwordless authentication, adaptive security, and advanced fraud prevention, Mosaic empowers businesses to enhance customer engagement, streamline onboarding, and protect user accounts—all while maintaining compliance and reducing operational costs.
Mosaic for Fraud Prevention empowers businesses to proactively detect and prevent fraud with cutting-edge AI and advanced analytics. From account takeovers to bot attacks and social engineering scams, Mosaic provides the tools to protect your business, streamline fraud investigations, and maintain trust—all while reducing costs and complexity.
Mosaic for Identity Verification delivers lightning-fast, highly accurate verification using advanced AI and ML. With support for over 10,000 ID templates, biometric matching, and fraud detection, Mosaic simplifies compliance, protects privacy, and scales effortlessly to meet the demands of global businesses.
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Leading US Bank Achieves 1300% ROI with Transmit Security Fraud Prevention Service
Increased bot detection rate
Decrease of false positives and false negatives
Leading US Bank Achieves 1300% ROI with Transmit Security Fraud Prevention Service
Increased bot detection rate
Decrease of false positives and false negatives
Leading US Bank Achieves 1300% ROI with Transmit Security Fraud Prevention Service
Increased bot detection rate
Decrease of false positives and false negatives

Leading US Bank Achieves 1300% ROI with Transmit Security Fraud Prevention Service
Increased bot detection rate
Decrease of false positives and false negatives
Leading US Bank Achieves 1300% ROI with Transmit Security Fraud Prevention Service
Increased bot detection rate
Decrease of false positives and false negatives
Transmit Security Ranked as a ‘Leader’ in The Forrester Wave™: Customer Identity & Access Management (CIAM) Solutions, Q4 2024
Featured in Liminal’s Link Index for Account Takeover Prevention in Banking: Leading Vendors
© Copyright Transmit Security. All Rights Reserved. Privacy Policy | Terms of Service
© Copyright Transmit Security. All Rights Reserved. Privacy Policy | Terms of Service