Every year at Gartner IAM, we hear new buzzwords and concepts that catch our attention, luring us to attend another analyst session. This year, the agenda teased us with terms like, “continuous authentication,” “passive behavioral biometrics,” “invisible MFA,” “device profiling,” “identity threat detection and response” and “journey-time orchestration.” As you might guess, it’s all inter-related and falls under an umbrella term (and theme of the event) “identity-first security.”
Granted, buzzwords can’t solve the problems you face with customer account takeovers, fraudulent account opening, CIAM complexity and silos. It’s the technology behind the curtain that you need to understand and implement. So let’s make sense of it all. This article will define these terms and why analysts now recommend more advanced capabilities as a key component of any modern CIAM stack.
In this post, I’ll also highlight the top 5 Gartner IAM analyst talks (our favs) that cover these concepts — repeatedly. By the end, you’ll have a set of analyst recommendations and key takeaways that’ll empower you to modernize your customer identity strategy.
The convergence of identity and security
In the Gartner IAM talk titled, ”Avoid the Breach With Identity Threat Detection and Response,” Gartner Sr. Analyst Henrique Teixeira pointed to the massive SolarWinds breach as a wake-up call in 2020 that prompted a major change in how we view identity and access management (IAM). It became a clear directive for identity to play a central role in cybersecurity.
The fact is, security operations center (SOC) teams are stretched thin, overwhelmed by a breadth of signals across endpoints, applications, servers and networks. They see risk events but without enough depth. And until recently, identity teams didn’t have threat detection as an integral part of their identity stack. Fast forward to 2023: identity and access management is the 2nd fastest-growing spend in cybersecurity.
How Gartner defines “identity-first security”
In the session, “Identity-First Security as the North Star for Your IAM Reimplementation,” Gartner VP Analyst Mary Ruddy defined identity-first security as, “an approach that makes identity-based controls the foundational element of an organization’s cybersecurity architecture.” Ruddy described identity-first security as “the end goal” and the most important aspect of your Zero-Trust strategy.

Ruddy presented the guiding principles of identity-first security — the three Cs:
- Consistent – e.g. requires MFA for all users, devices, apps and use cases
- Context-aware – e.g. uses device profiling, passive behavioral biometrics, threat intelligence, etc.
- Continuous – e.g. assesses risk and trust at all times; some call this continuous authentication or invisible MFA
There are a number of buzzwords I’ve included here, so as promised, I’ll break it down for you, but first: why is any of this necessary?
MFA is not enough
Three factors are driving the need for identity-first security that’s consistent, context-aware and continuous:
- One point in time – Traditional authentication only checks the user’s identity at a single point in time.
- Variable LOA – Not all MFA achieves the same level of assurance (LOA). True passwordless authentication with a fingerprint or facial biometric provides the strongest assurance, but the LOA declines from there with magic links, OTPs, social logins or knowledge-based questions. Your risk goes up as the assurance drops.
- Advanced threats defeat MFA – Multi-factor authentication (MFA) is stronger than single-factor, but threat actors are proving it’s still possible to take over accounts before, during and after login.
In the talk titled, “The State of User Authentication, 2023: What it Is, Why It Matters, How It Will Change,” Gartner Sr. Director Analyst Ant Allen explains the risks of MFA:

What is continuous authentication?
A solution for weak MFA is something analysts are now calling continuous authentication — an umbrella term which includes device profiling, passive behavioral biometrics, applied threat intelligence, reputation services and more. You may encounter other terms to describe this same concept, depending on the vendor and analyst. Some call it passive authentication or invisible MFA. At Transmit Security, we call it continuous risk and trust assessment as part of our Detection and Response Services. Regardless, this advanced security is needed to prevent today’s sophisticated threats, like man-in-the-middle attacks and session hijacking.
The idea is that we need continuous authentication to constantly assess what the user is doing beyond the login itself. For example, is it normal for this customer to access these services or transfer funds at this time of day or location from a new device? In order to assess risk in real time, you first need to build a complete profile of your trusted customer. Once you know how the customer typically behaves, you can use this as a benchmark and compare it to journey-time signals — across the entire session.
In the same talk on user authentication, Ant Allen explained, “User authentication is not just a gatekeeper. Evaluate recognition and risk signals continuously through the user journey.” Allen further states, “User authentication is a journey-time process that provides credence in an identity claim by a person already known to the organization.”

What role does device profiling play?
In the talk titled, “Stopping Account Takeover Attacks,” Gartner VP Analyst Akif Khan described device profiling as a form of passive authentication, which requires no action by the end user. Instead, fraud detection solutions are able to assess if the device is trusted, risky or suspicious by examining all that can be seen or known about the endpoint.
Khan presented this slide to further explain:
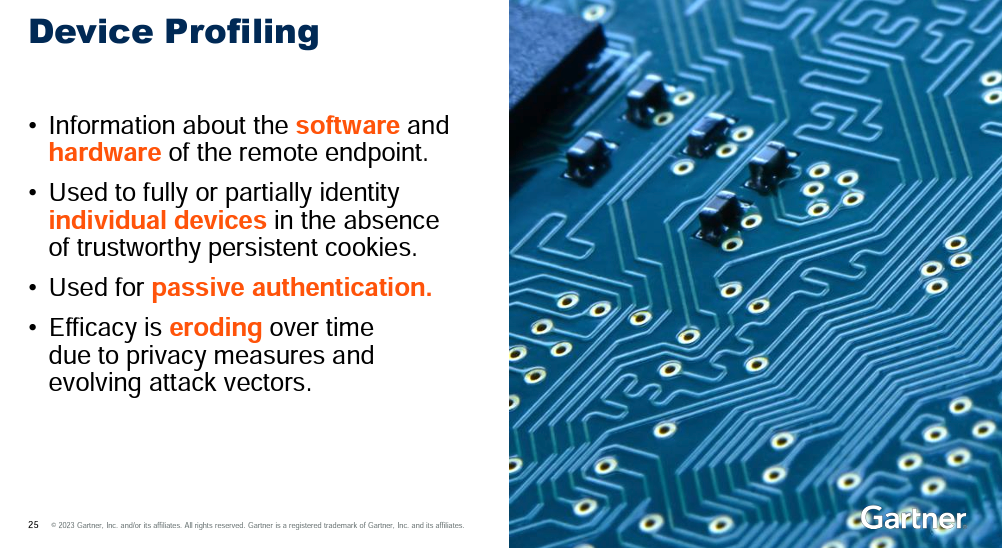
In reference to the last bullet above, it’s true that, in most cases, the efficacy of device profiling is eroding due to privacy measures. To overcome this obstacle, Transmit Security has developed more advanced privacy-age device fingerprinting. Read our service brief to learn more.
What is passive behavioral biometrics?
As the term implies, passive behavioral biometrics looks at the user’s behavior throughout an active session without asking the user to prove who they are again and again. Passively assessing the user’s behavior improves the customer experience and your security posture simultaneously.
By collecting signals, the solution can assess if the user’s behavior is consistent with their trusted user profile. Any signal that strays from the norm is weighed as part of a holistic risk analysis. You can look at a wide range of location intelligence, potentially combining IP, Wi-Fi and GPS signals to detect and prevent spoofing attempts, for example.
Likewise, event intelligence is used to compare journey-time activity to threat intelligence and typical user behaviors. Are they scrolling, typing and clicking like a human or a bot? Passive behavioral biometrics can give you the answer.
Orchestration pulls it all together
When it comes to risk management, you now have many solutions in your CIAM stack:
- Identity proofing
- Authentication
- Authorization
- Fraud prevention
- Bot detection
You may have solutions from many vendors, and they’re giving you different signals and different risk scores. In this scenario, you’re going to struggle with data silos, complex integrations, security gaps and a disjointed user experience. To solve these problems, you need a way to combine all of the solutions and signals to make accurate decisions based on what’s happening in the user journey.
In a session titled, “Use Journey-Time IAM Orchestration to Deliver Better UX,” VP Analyst Akif Khan states, “Orchestration solutions manage vendor integrations and deliver a unified control layer.” In other words, orchestration brings all of the pieces together and uses a policy engine to then come up with an overall risk assessment and trigger an accurate response at any point in the user journey. With the right orchestration solution, you should be able to deliver a tailored and dynamic risk-based identity journey.
Transmit Security = security-first identity
That’s right, we flipped the words for emphasis. If you visited our booth at Gartner IAM, you may have seen “Security-First Identity” emblazoned on the wall. Unlike most CIAM vendors, we’ve been a cybersecurity company since day one. Best known for orchestration and truly passwordless authentication, we’ve developed a state-of-the-art security platform to provide customer identity and access management (CIAM).
The Transmit Security Platform is uniquely designed to fortify security and optimize CX across the entire identity lifecycle — from onboarding to transacting. Continuous monitoring and analysis mitigate risk and elevate trust on the fly. By orchestrating the analytics layer, UX, identity and fraud services, the platform makes context-aware decisions and adapts user flows, triggering the right action at the right time.
Detection and Response Services combine passive behavioral biometrics, privacy-age device fingerprinting and threat intelligence — continuously assessing hundreds of signals and correlating the data to return a recommended action of Trust, Allow, Challenge or Deny. Machine learning and orchestration ensure it’s highly accurate, reducing false positives and false negatives by 90%.

Our top picks:
5 must-see analyst talks at Gartner IAM 2023
Finally, the list you want to see. Most of these sessions are listed — and quoted — above. But first, a disclaimer: I was not able to see every session, and I prioritized customer identity and access management (CIAM) above all else since that’s our specialty at Transmit Security.
Anyone with an “Attendee” badge and login can still play these sessions recorded on audio and view the slide decks by logging into the Gartner IAM Navigator app:
- “Stopping Account Takeover Attacks” with Gartner VP Analyst Akif Khan
- “Technical Insights: Improve Customer Identity Corroboration With Passive Behavioral Biometrics” with Paul Rabinovich, Gartner Sr. Director Analyst
- “The State of Customer IAM, 2023” with VP Analyst Mary Ruddy
- “Use Journey-Time IAM Orchestration to Deliver Better UX” by VP Analyst Akif Khan
- “Avoid the Breach With Identity Threat Detection and Response” by Gartner Sr. Director Analyst Henrique Teixeira
Find out how you can implement these analyst-recommended techniques with an easy-to-implement solution that’ll speed time to value.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.



