Applications give customers the user experiences they want, like shopping online or accessing healthcare records. While developers focus on the security of the application, users bear the burden of securing their access to the application. Unfortunately, cybercriminals recognize that user access can be a weak link in an application’s security posture. Increasingly, malicious actors target application access as a way to steal PIII or credit card data.
Attacks targeting access and credentials impact a company’s security posture and lead to costly fraud. According to the Verizon 2021 Data Breach Investigations Report, phishing and the use of stolen credentials were the top two attack action varieties leading to data breaches. Further, the Federal Trade Commission received 2.8 million consumer fraud reports in 2021 that totaled more than $5.8 billion in losses.
In response, many companies use Magic Links as a passwordless authentication method. While Magic Link authentication can help mitigate risk, it still comes with some security weaknesses that organizations need to consider before implementation.

How Magic Links work
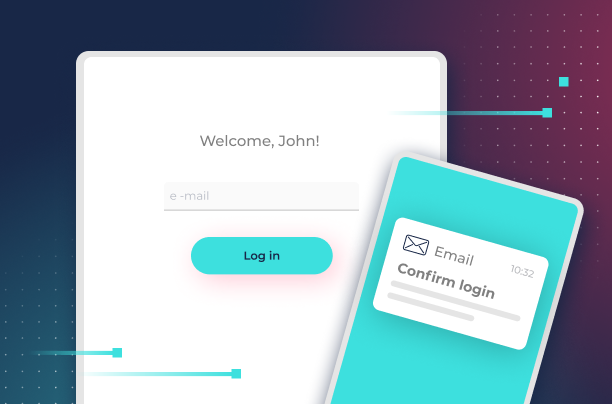
A Magic Link involves a three-step process like the one people follow to request a one-time-password (OTP) when they forget their password.
The process looks like this:
- User inputs their email in the application’s login
- Application sends an email with a link containing a token and hash function
- User clicks on the link in the email to access the application
The Magic Link gives the app developers a way to build multi-factor authentication into the process. The user has their email password to access the link (something they know), and the device used to access the email is something they have.
What are the benefits of Magic Links?
Most customer-facing applications rely only on a login ID and password. Often, businesses can’t enforce multi-factor authentication, creating security and fraud risks. Magic Links help overcome many of these security and customer issues.
Enhanced security
As a passwordless authentication method, Magic Links reduce the risks associated with poor customer password hygiene. Meanwhile, customers don’t have to worry about creating another unique password that they need to remember.
Easy to use
The customer onboarding experience is seamless. They register the same by providing an email. The only difference is that they need to check their email instead of creating a password. The app developer sets the Magic Link’s authentication controls for a single session or multiple sessions.
Easy deployment
Magic links can be easily deployed using an API or Auth0. Developers can set the authentication parameters and customize the link’s expiration time. With a few lines of code, developers can rapidly set up more robust security features without increasing the time to market.
Reduced IT burdens
Since there’s no password involved, users won’t need to reset a forgotten password, reducing IT help desk burdens. Additionally, Magic Links reduce failed login attempt alerts, ultimately reducing noise.
Improved customer experience
The one-click login streamlines the customer experience, leading to more conversions and better customer retention.
Are there security concerns with Magic Links?
Although Magic Links enhance security, they’re not a perfect solution. Companies that use a Magic Link for authentication still need to consider several weaknesses.
Insecure email
In 2021, the FBI received 19,954 business email compromise complaints. If a consumer’s email has been compromised or spoofed, the Magic Link is also compromised.
Lack of clear best practices
Although developers can customize the link’s expiration time, they have no best practices to follow because no official standards for Magic Links exist. Balancing user needs with security can lead to inconsistent practices, creating security and compliance risks.
Multiple requests
Sometimes, the email containing the Magic Link will be marked as spam by the email provider. If the user doesn’t check their spam folder, then they might request an additional link, creating multiple tokens. Not only does this frustrate the customer, but it creates an additional security issue if the email has been compromised.
Loss of device
Part of the security model built into Magic Links is that the user controls the device, giving the app developer the ability to enforce a “something you have” authentication step. If the user loses the device without having the appropriate password or biometric login controls on it, then the Magic Link capability is compromised because someone has access to the app, device, and email.

Creating True Passwordless Authentication with Transmit Security
Magic Links mitigate risks associated with poor password hygiene, like reused or weak passwords. Many organizations continue to use them as a way to enhance security even without official best practices. For organizations that continue to use Magic Links, setting link expiry for 15 minutes can help.
However, Magic Links remain a relatively weak form of passwordless authentication since malicious actors can still engage in brute force attacks or use email account takeovers to circumvent these measures.
Organizations need more robust passwordless authentication methods that incorporate biometric authentication through the user’s device. Transmit Security passwordless authentication creates a single customer identity and incorporates a device’s biometric capabilities, like fingerprint or face ID. By using the device’s biometric scanner, any issues associated with email compromise and loss of the device are resolved.
Final thoughts on magic link authentication
By using a combination of open standards and device biometrics, organizations can create easy, secure, and portable customer authentication while retaining the benefits associated with Magic Links.



