Yes, it’s an inconvenient truth: IAM and CIAM are distinctly different. Identity and access management (IAM) built for the workforce is simply not designed to meet the needs of customers. When companies try to bend IAM to achieve customer identity and access management (CIAM) objectives, they eventually realize it doesn’t work like they need it to.
Using IAM for customer use cases may seem logical. After all, the core building blocks of IAM and CIAM appear to be the same: authentication, authorization, real-time account protection and user management. But the requirements for IAM and CIAM are either misaligned or incompatible.
In this article, I’ll first explain what CIAM should accomplish and how it’s done right. Then we’ll explore 8 key differences between IAM and CIAM. In the end, I’ll link you to our white paper to give you a deeper understanding of every requirement and nuance.
What should CIAM achieve?
If you’re thinking of using IAM for customer use cases, first consider all you must accomplish. CIAM that’s purpose-built for customers is designed to manage, secure and (ideally) unify customer identities, authenticate them with high assurance and authorize their access to resources — all at scale.
Customer expectations dictate additional functionality like social logins, multi-device support, omnichannel experiences, ease of use and a consistent brand UX. Core functionality should also provide customer self-service registration, privacy and consent management and personalized experiences.
To protect against account takeover (ATO) fraud and synthetic account creation, analysts also recommend identity verification, true passwordless authentication plus continuous adaptive trust (CAT) to assess and mitigate risk at all times. Very few CIAM solutions deliver it all, and IAM offers only a small fraction of these customer requirements.
IAM or CIAM: 8 key differences
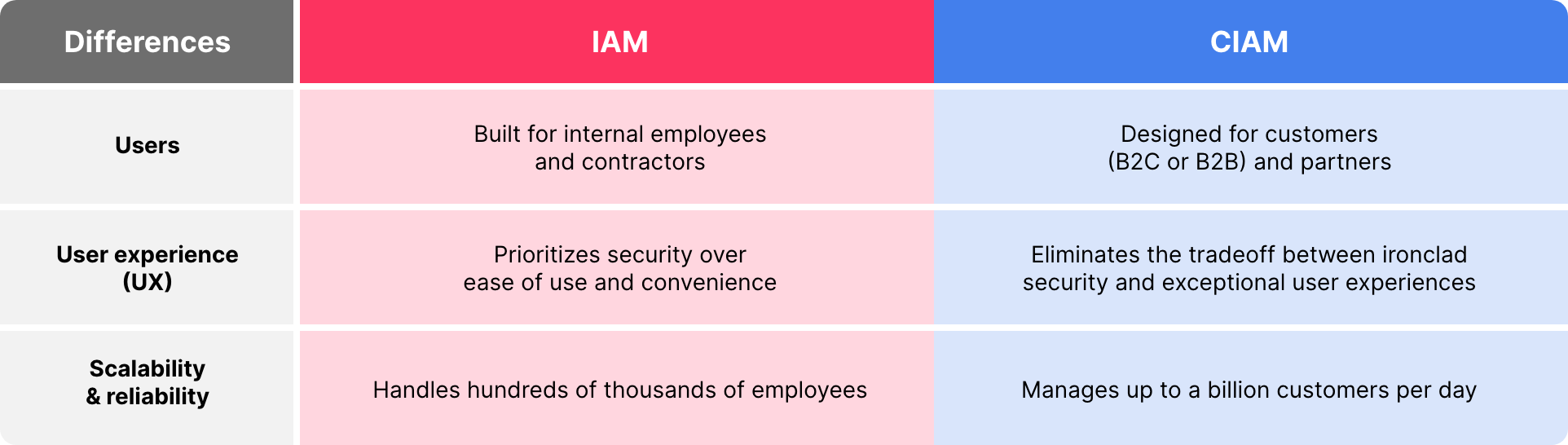
There are 8 key differences born from the reality that IAM is built for internal employees and contractors whereas CIAM is designed for customers and partners. IAM solutions were first created on-prem to improve corporate security, ensure productivity and streamline access to work applications. More recently, some IAM vendors have worked to refine their UX, and many have migrated to the cloud. Nonetheless, IAM is far more restrictive, prioritizing security over UX in most cases.
Security is a top priority for customers too. The key difference for customers is twofold:
1) customers will not tolerate a poor UX in exchange for security; 2) customers bring more careless behavior and higher risk. They need it all. CIAM must fortify security and ensure privacy while delighting customers with smooth and easy experiences. On top of that, CIAM must scale to support millions of customers and the full range of devices and channels, all without downtime or delays.
IAM or CIAM: UX and scalability
Comparing the user experience and scale of IAM to CIAM is like comparing a submarine to a cruise ship. The submarine is not designed for comfort nor capacity. It has a job to do — and so does everyone on it. The cruise ship, however, is built for luxury, designed to keep passengers safe, happy, comfortable, and even pampered. Top-notch service is expected.
Your customers want to be treated like passengers on a luxury cruise, and they won’t suffer delays, downtime or poor experiences. CIAM must be able to manage millions to even billions of identities and process tens of billions of logins per day. Scalability and reliability are baseline requirements that are part of the experience customers demand.
With an emphasis on optimizing the UX, CIAM requires cloud-native solutions (not on-prem or cloud-migrated) that can deliver the scalability and reliability required. IAM solutions are simply not built to support and delight millions of customers.
IAM or CIAM: Devices
Number three on our list of eight key differences: devices. Most organizations maintain some control over the devices and apps employees use. Mobile device management (MDM) tools make it possible to set and enforce policies that mitigate risk for the workforce.
By contrast, organizations have almost no control over the devices, operating systems, browsers and applications consumers use. These customers are also accessing a wide variety of public-facing channels: websites, apps, online stores, brick-and-mortar, call centers and kiosks. For customers, there is no linear path, and they enjoy the freedom of engaging with your business as they please.
So far I’ve presented 3 key differences: UX, scalability and devices. These factors invoke major differences in the capabilities needed to serve and secure customers. For a deeper look at all 8 key differences, read our white paper on IAM and CIAM.
Why CIAM is a competitive differentiator
Organizations that use workforce IAM for both use cases miss out on the enhanced feature sets the market is building for customers. At best, using IAM for customers meets the lowest common denominator of requirements. Baked-in limitations make it difficult to differentiate and keep pace with application owners and identity architects who gain the advantages of modern CIAM solutions.
Companies now have a chance to get it right with a CIAM solution designed from the ground up for customers. Businesses that leverage a cloud-native CIAM service benefit from continuous innovation designed to reduce friction and fraud. Now more than ever, competitive differentiation leans heavily on UX and security, making purpose-built CIAM a strategic imperative.
Why prioritize CIAM over IAM projects?
Customers are the true power brokers who determine how companies compete and win. They’re the driving force behind today’s digital transformation and CX trends. Consumers simply want quick and easy access to their accounts, customer support and all that’s available to them. They also want their accounts and data to be secure, but consumers tend to introduce more risk than employees. Business success depends on how well and how fast companies deliver on all customer demands.
Final thoughts on CIAM and IAM
Even if your IAM solution works great for employees, it’s no replacement for modern CIAM that’s built from the ground up for customers. A cloud-native CIAM platform empowers you to optimize the customer experience and fortify security while achieving limitless scale and reliability. If done right, you can also accelerate passwordless adoption, streamline omnichannel experiences, support all devices and give customers easy access to all that your business offers.
Read our white paper on IAM and CIAM for a deeper understanding of how to meet the 8 unique needs of customers.



