An appropriate analogy for the modern fraudster is a “kid in a candy store.” They’re surrounded by tools and targets with minimal threat of accountability or consequence. Digital fraud is now less risky, simpler, and more accessible — and the financial motivations have never been clearer. Cybercriminals have always targeted the financial sector, but modern fraudsters can cash in on vulnerable bank accounts without ever learning a line of code.
With the widespread adoption of online banking (71% in the United States alone, including 95% of Gen Zers), a fraudster’s choice of potential targets has risen precipitously. The payday can be tremendous even for a single attack, and cumulative business costs are soaring to staggering levels. One estimate by Juniper Research suggests worldwide cybercrime losses will crest $5 trillion in 2024.
This sum may be daunting, but today’s easily accessible fraud tools make it more than believable. Cybersecurity watchdogs have witnessed the development of “fraud communities,” which strive to uncover and exploit vulnerabilities in digital infrastructure. Once they discover a vulnerability, it can be automated, packaged, and sold (or given away for free). These communities are becoming so common that criminals without technical knowledge can merely follow a tutorial to reel in a sizable income.
This article exposes how these communities help fraudsters deploy attacks with minimal technical knowledge. However, please take note: although we’re about to outline how easy it is to commit digital fraud, we’re intentionally leaving out important details.
We refuse to educate or encourage new fraudsters. Fraud is a crime that victimizes innocent people. Full stop. Our purpose here is to educate you about the threats businesses and customers face.
With that said, read on to learn more about how fraudsters learn their trade — and why fraud will only worsen as these tools become more accessible.
Real-life fraud doesn’t require technical skill
The general public relies on films and television for their knowledge of hackers. While some media might portray genuine hacking or social engineering methods, the average person still imagines fraudsters as hoodie-clad tech whizzes churning out code in real time.

While some hackers possess exceptional coding abilities, you don’t need training or skill to attack an account. You only need to know where to obtain the tools or how-to guides. Many sources store information and downloads for novice hackers: Telegram groups, darknet markets and forums, Discord servers, and even surface websites.
These communities provide general knowledge of the cybercrime ecosystem and offer step-by-step lessons on buying stolen credentials, obtaining phishing tools, increasing your success rate, bypassing traditional security measures, and avoiding detection by the authorities.
A quick jog in a brand-new fraudster’s shoes
Let’s pretend you chose to forfeit your morals and become a hacker. You set your sights on the world of fintech because you (rightly) assume there are plenty of poorly secured accounts with lots of cash. You know that success is just a matter of finding them and getting out with the money.
First, you need to learn more about committing fraud — but don’t worry, it won’t take long. You only need to ensure you can cash out easily, and you should probably figure out how to keep your tracks under the radar. Luckily for your new fraudster persona, this information is readily available.
The fastest and biggest source of information is Google. Remember, you’re not a technical expert, so you’d probably start by Googling “how to hack bank accounts.” The knowledge you find will be limited, or you will need to drill down very deep to find anything practical. Moreover, the SafeSearch feature of Google may block a few results related to the subject. However, you will find enough to move forward with your new occupation. Google’s censorship is not a roadblock.
Thanks to guidance from surface websites, you quickly discover that the most accessible platform to learn fraud is Telegram. If you’re unfamiliar with Telegram, it’s a messenger app that gained a reputation for its security architecture and lack of content moderation.
Telegram is a paradise for learning about cybercrime because you can search for topics that Google might hide, and it’s mostly hidden from the authorities. Telegram’s end-to-end encryption provides easy anonymity for budding cybercriminals with minimal setup.
Some groups are a bit hard to find, but with simple search terms like “fraud,” “fraud tutorial,” “bank logs,” and “card drop,” you can begin combing for tools. From there, you dive deeper for more informative groups.
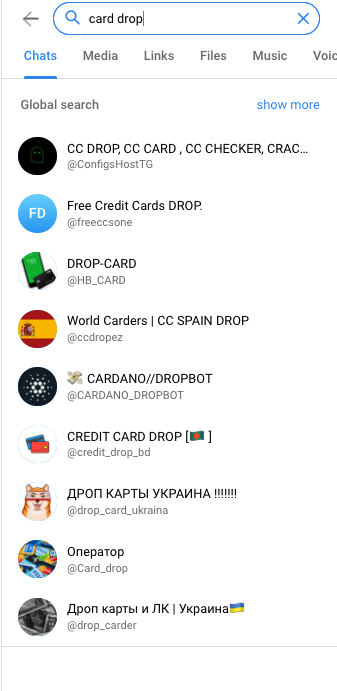
Get in, fraudster, we’re going shopping
So, you decided to give in to the dark side, but you want cash in hand. After some quick searches on Telegram groups, you ponder your preferred attack vector. You realize getting a cash advance from an ATM might not always work, especially using credit card numbers not issued in your country.
You consider targeting ecommerce. You’ll have to monetize anything you get, meaning you must sell off the physical goods or e-products you acquire. You can convert them to legal tender, usually by selling them on online marketplaces — both legitimate and illegitimate. But that’s a lot of extra work, and you’d prefer to go straight for the source.
After a little deliberation, you decide to do a “quick hit,” also known as an account takeover, on a bank account. You’ll get access to an account, transfer funds from a victim to yourself, and disappear. Because you’ve been scouring Telegram groups, you already know where to find the tools and tutorials to do just that.
The group in the image below shows you how and where to purchase “bank logs,” or credentials for bank accounts containing funds you can transfer.
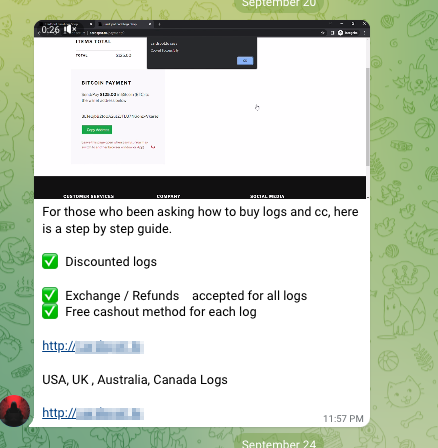
This group refers you to a marketplace with UI design that resembles leading e-commerce websites.

As you explore the storefront, you’re treated to a video guide that showcases everything you get with your purchase. In addition to login details, you’ll receive instant cookies, which will be useful for avoiding detection by digital security vendors.
A smooth purchase later, and you’re the proud owner of some stolen bank credentials. What now? You follow the guide on successfully logging in, of course:
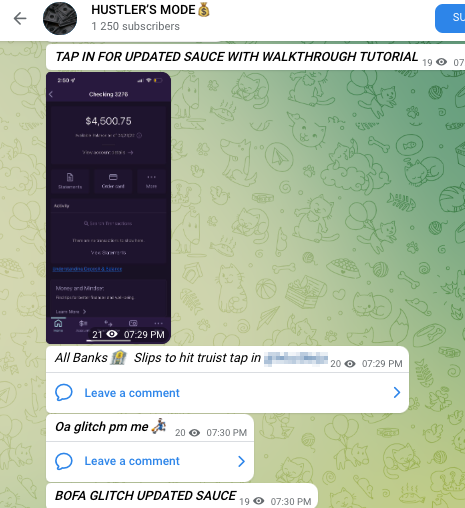
Next, you’ll want to be smart about how you transfer the money out of your victim’s account. You can’t directly withdraw from the stolen account since you don’t have a debit or credit card related to it. Transferring the money to your personal account will lead the authorities straight back to you. How do you get the money out?
You need a “bank drop.” A bank drop is a clean account where you can transfer money without raising suspicion. It acts as a mule or middleman, allowing you to move the funds to your own account after several hops between dummy accounts. You’ll likely use at least a few bank drop accounts to cover your tracks.
Bank drop accounts are typically opened through online banks. This type of fraudulent account is referred to as a “bad actor account.” Fraudsters will open seemingly legitimate accounts and keep them clean of criminal activity for a while to avoid suspicion. Then, they’ll bounce stolen funds between them before any red flags can be raised. So, where do you get your bank drop?
You have two options:
The first option is using a third party, usually a paid service or another fraudster who will do it for us. We can seek out relevant vendors or fraudsters offering their services with the same technique we used before.
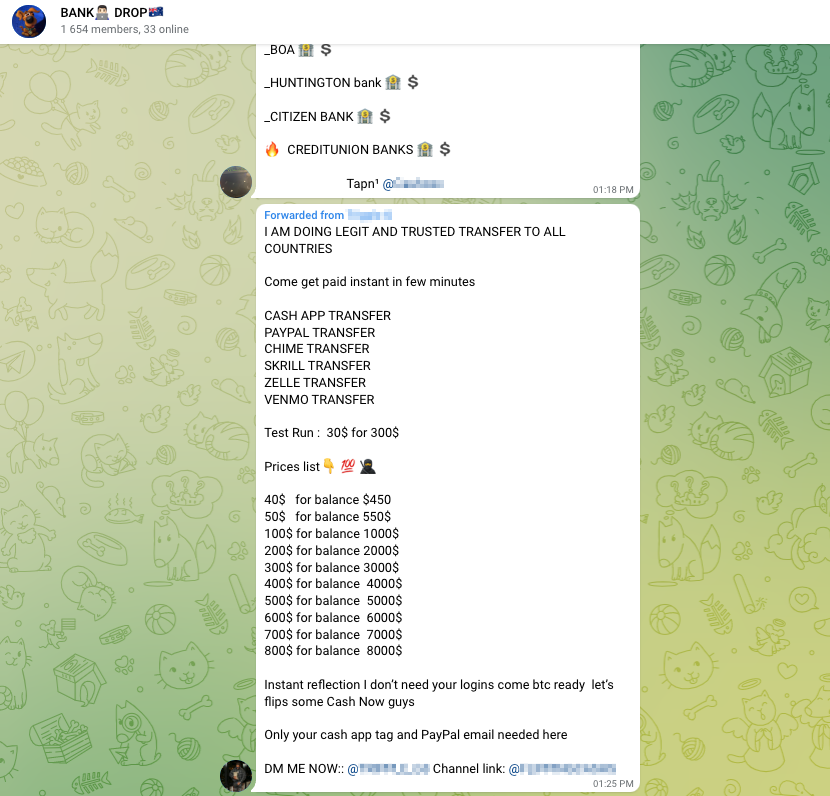
The second option is doing it yourself by purchasing bank drop login details:
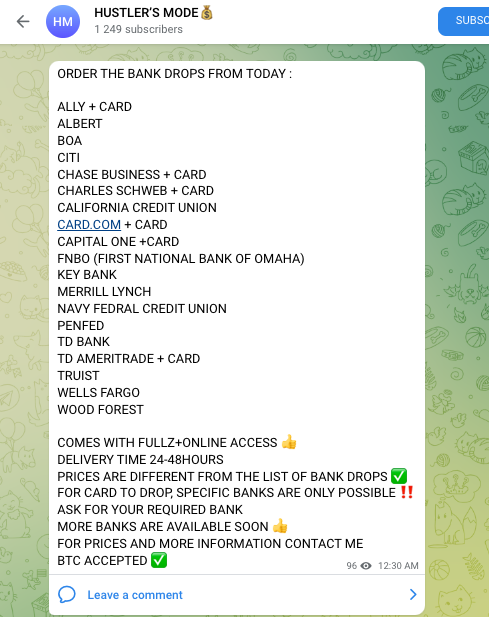
Like a kid in a candy store
You finally transfer the money to your final endpoint. This could be a bank account you opened for personal use or another bank drop that allows you to withdraw money without a card. Now it’s time to don your hoodie, go to your local ATM, and get the cash.
The customers of banks and financial organizations are always in attackers’ crosshairs. As we just saw here, the low barrier to entry into the cyber-fraud ecosystem poses an imminent threat. Threat intelligence and constant research are crucial to catching up with rapidly changing attack vectors and trends. Unfortunately, there can be no doubt that fraud will continue to rise.
While a few hackers are content to facilitate fraud by simply selling credentials, tools and tutorials, many more criminals — including those with minimal technical knowledge — will jump at the growing opportunities within the digital fraud ecosystem. All it takes is time, a bit of luck, and a willingness to break the law.



