With the increased usage of mobile devices for sensitive transactions, including banking and working, the threat of mobile device fraud has grown significantly, requiring the use of advanced detection methods to distinguish between legitimate and fraudulent users on mobile devices. In our last blog in this series, we discussed the growing threat of mobile fraud, attack methods, and benefits of native SDKs for improving mobile fraud detection.
To meet this need, Transmit Security has developed native Detection and Response SDKs for both iOS and Android applications that enable us to retrieve large amounts of device metadata that can be used to further distinguish between legitimate users and fraudsters using various device manipulations that target mobile applications and devices.
Part one of this blog series explained the use cases for mobile native detection. In this second blog post on our mobile native detection series, we’ll provide an overview of how our iOS and Android SDKs can be used to detect emerging fraud techniques, such as the use of app cloning, proxies and VPNs, device rooting and mobile emulators.
The need for native Android and iOS SDKs
Due to the differences between iOS, Android and web technologies, separate teams are often needed to build, test and manage iOS, Android and web applications and keep them updated as new OSes and devices are released. This effectively triples the work of development and maintenance and requires specialized knowledge that may be difficult to fill due to skills gaps.
Vendors that offer web, Android and iOS SDKs simplify the complexity and time needed to integrate and maintain their services with prebuilt functionality that is compatible with specific platforms and ongoing updates that work with the latest OS and separate documentation.
With regard to mobile fraud, some of the key differences between iOS and Android ecosystems that impact detection and response include:
- Closed vs. open ecosystem: iOS is a closed ecosystem, whereas Android is open-source, which can make it more vulnerable to attack.
- Models and configurations: Android devices have a wider range of device models and configurations, with some device manufacturers providing additional security features, whereas iOS devices have more uniform configurations and models that can make it difficult to maintain persistent device fingerprints for identifying trusted devices. In addition, Apple imposes greater restrictions around persistent identifiers in iOS devices. There are also fewer and less complex data points available in iOS devices compared to Android, which restricts the ability to run scripts and tests to retrieve more information.
- Third-party app installations: Android users can change their settings to allow installation from third-party app stores, whereas it is more difficult to do so on iOS devices.
App cloning
App cloning is the act of running multiple instances of an app on the same device, giving fraudsters the ability to perform parallel attacks or use a single device for distributed attacks that appear to originate from multiple devices.
By creating a sandbox, which is a separate and isolated environment in which an application can run without affecting other applications, attackers can run multiple app instances with different parameters or configurations or even degrade security measures like device fingerprints since it enables the use of environment variables that differ between the original app and the cloned one.
To detect app cloning, our researchers examined and installed various apps, including native applications like Samsung’s “Secret Folder” and third-party apps for iOS like “Dual Space” and ran our SDK through those apps to search for anomalies in our raw detection data points. In iPhones, it is also possible to clone apps without an external app on jailbroken devices. With this information, we were able to detect and isolate usage of cloning and sandbox apps that run our SDK.
Network mismatches
As part of the extra data points we can collect via our Android and iOS SDKs, we receive information on the cellular network of the device, including the network operator, SIM code, network name and country code.
Using this data and external enrichment services, we’re able to look for mismatches between the information received and the enriched information — for example, comparing the operator country code that is retrieved from the SDK with the corresponding country code from the enrichment service or comparing the mobile network data with enriched IP data. By comparing this information, we can detect anomalies that may indicate non-legitimate device manipulation.
Rooted and jailbroken devices
Rooting is a process that allows you to attain root access to a device’s Android operating system code. Although rooting Android devices could be used for legitimate purposes to customize system settings (albeit rarely, and only by expert users), rooted devices are considered to be high risk since they give fraudsters the ability to modify the device’s software code or install other software that manufacturers would normally block for security reasons.
The equivalent term for rooting on iOS devices is jailbreaking. Although Android devices are highly customizable, iOS devices have limited customization unless jailbroken. Whereas some Android manufacturers may allow rooting devices, Apple takes steps to prevent jailbreaking, which requires the exploitation of vulnerabilities in the device’s hardware or software.
Both rooted and jailbroken devices present significant security risks, as they expose parts of the device that would otherwise be secured and make the device more susceptible to malware. As a result, the detection of rooted and jailbroken devices is crucial for risk and fraud mitigation.
At Transmit Security, root detection is performed using various tests and searching for specific device metadata that indicate handling with the operating system. These indicators may include specific apps or malicious paths and permissions that would not be installed on a clean device.
Emulator and simulator detection by sensors
Mobile emulators are software tools that are installed on PCs to simulate a mobile device’s hardware and software environment, as shown below.
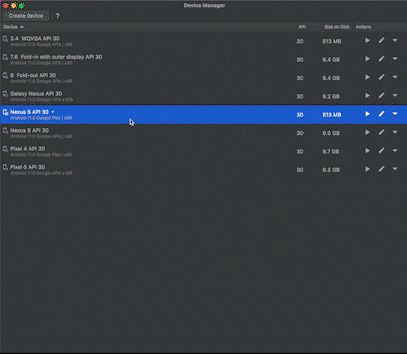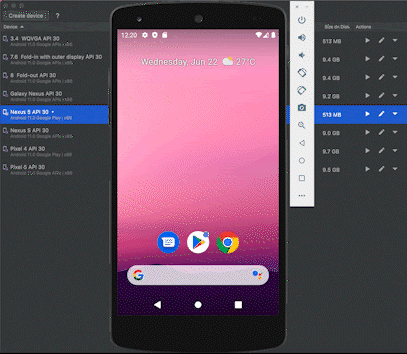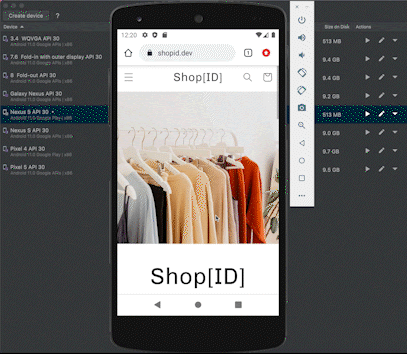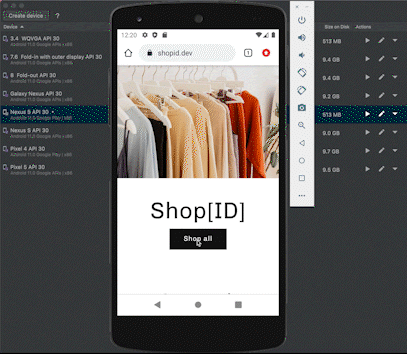
Although emulators can be used for legitimate purposes, like gaming or mobile app development and testing, fraudsters are increasingly using mobile emulators to test and bypass security measures by posing as legitimate or trusted devices.
While emulators are widely available for Android devices, Apple doesn’t allow video emulators on its official App Store, making them less common and harder to install on iOS devices. However, emulators can be run on iOS devices without jailbreaking them in order to test apps on virtual devices using mobile simulators. Simulators are similar to emulators as they are installed on PCs to replicate the complete software environment that an app will run in, including all of its configurations and variables — just not the hardware features, as emulators do.
It may also be more difficult to detect emulators and simulators on iOS devices compared to Android devices. This is because iOS simulators are designed to be nearly identical to physical iOS devices in terms of software behavior and performance, whereas Android emulators often have distinct differences in behavior and performance due the wide variety of manufacturers and customizations of Android devices.
In addition to the Android emulator detection that is enabled by our Detection and Response web SDK, the mobile SDK allows us to retrieve the device’s sensor information, such as touch pressure, swipe patterns, and typing speed, which enables emulator detection. To help detect emulator use in Android devices, we ran our SDK on various emulators, from the standard developer emulators like Android studio to more aftermarket ones that are used in the gaming industry.
For detection in iOS devices, we check certain parameters in the operating system environment, like file paths, runtime parameters and available resources like storage and memory. Through these processes, we are able to recognize specific patterns that allow us to determine with high confidence whether or not a mobile emulator or simulator is being used.
Improving Detection and Response with Transmit Security
Transmit Security’s Detection and Response mobile SDKs for iOS and Android can help prevent fraud by retrieving additional device metadata that distinguishes between legitimate users and fraudsters who are using app cloning, network evasion tactics, device rooting and emulators to bypass security measures.
To find out more about our mobile SDKs for risk, trust, fraud, bots and behavior detection, check out the documentation or read our service brief on our Detection and Response Services to discover how it can benefit your business.