Credential stuffing takes advantage of password reuse to allow an attacker to hijack a user’s online accounts. If someone uses the same password across multiple websites or online accounts, then a breach of user credentials from one of these sites could allow an attacker to access all accounts that use the same credentials.
What is Credential Stuffing?
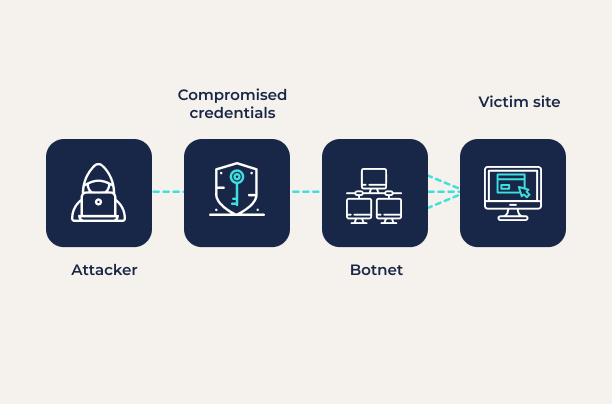
A credential stuffing attack takes advantage of the fact that many people reuse the same or very similar passwords across multiple online accounts. A credential stuffing attack starts with the exposure of a user’s password for an online account via a data breach, phishing attack, or other means.
Once an attacker has this password, they’ll try to use it to authenticate to other online accounts. For example, a password from a social media account may be used on other social media sites, email accounts, financial institutions, etc. Attackers will also commonly try to authenticate as the user to corporate email and other accounts.
With credential stuffing attacks, a reused password is only as strong as the weakest account using it. Password reuse across multiple sites could give an attacker the ability to access online banking and corporate email accounts after a data breach at a minor website where someone created an account.
Credential stuffing attacks can be easily automated using a botnet. As a result, they are one of the most common cyberattacks. Bots can be provided with long lists of compromised credentials and target websites and will work through them, identifying any accounts for which passwords were reused.
Example of Credential Stuffing
In 2021, customers of Verizon Visible, the mobile operator’s budget offering, were the victims of a credential stuffing attack. The attacker used a credential stuffing attack to gain access to the accounts of the company’s customers and then used their stored payment card or account information to order new iPhones that were then shipped to the attacker.
Credential Stuffing vs. Brute Force Attacks
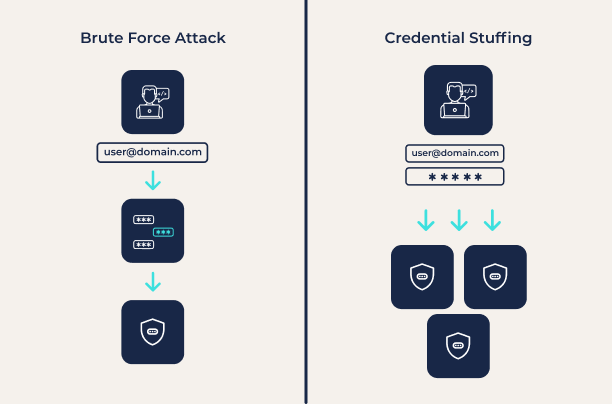
Credential stuffing and brute force attacks are both forms of password guessing attacks. However, they take very different approaches.
Credential stuffing attacks take advantage of the fact that most people have poor password security and reuse passwords across sites. In fact, a Google survey found that 65% of people reuse passwords across multiple accounts. This means that an attacker with a verified password for one account has excellent odds of finding another account with the same login credentials.
A brute force password guessing attack, on the other hand, is designed to find passwords by trying every possible combination. While this is guaranteed to succeed eventually, it can take a very long time, and the password may be changed before the attacker succeeds. The effectiveness of these attacks depends on the password length, the algorithms used to securely store a password, and whether the attack can be performed online (via a web portal) or offline (testing against a breached password hash). In most cases, brute force attacks are too slow to be worth the effort.
Credential Stuffing Prevention
Credential stuffing attacks take advantage of the fact that people commonly reuse the same password across multiple different online accounts. The simplest way to protect against credential stuffing attacks is to use a unique password for every online account.
However, this does not protect against other password-related security risks. For example, having unique but weak passwords for each account might leave a user vulnerable to a dictionary attack, where an attacker tries to authenticate using a list of common words and passwords. Passwords are also vulnerable to phishing attacks, where an attacker attempts to trick a user into handing over their password.
Multi-factor authentication (MFA) can help to protect against credential stuffing attacks. By requiring multiple factors to log into an account, MFA makes it much more difficult to take advantage of a compromised password.
However, passwords are an inherently weak form of user authentication. The best way to prevent credential stuffing and other password-based attacks is to eliminate passwords altogether. Passwordless authentication, which authenticates users based on biometrics (fingerprint scanners, facial recognition, etc.) or possession of a trusted device, provides much stronger user authentication and complete immunity to credential stuffing attacks.